HIPAA compliance checklist: ensuring security in Healthcare
There is nothing more fundamental in the healthcare industry than HIPAA compliance. Your customers and partners need you, your product, or service to be HIPAA compliant. It’s like earning a Michelin star in the restaurant business—an assurance of quality, reliability, and commitment to excellence. In an increasingly interconnected healthcare domain, where the latest innovations such as the Internet of Things and Artificial Intelligence have an impact on healthcare data security, and data-sharing are ubiquitous, adhering to the Health Insurance Portability and Accountability Act (HIPAA) becomes more critical than ever.
Some interesting figures: As per the report by Compliancy Group, in April 2023 business associates reported 13 incidents that affected 4,077,019 patients, representing 92.2% of patients affected. Fines and consequences can range from $100 to $50,000 per violation (or per record), with a maximum penalty of $1.5 million per year for each violation. 60% were not fully confident they would pass a HIPAA audit. Only 34% had fully documented their HIPAA compliance. 99% find HIPAA compliance to be important to their business.

While data breaches and cybersecurity threats are rampant, protecting sensitive patient information is paramount. Compliance with HIPAA regulations is not just a legal requirement but also essential for maintaining trust with patients and avoiding costly penalties. This article provides a HIPAA compliance checklist, offering healthcare providers a roadmap to fortify their security measures and safeguard patient data effectively.
What is the key to HIPAA compliance?
According to HIPAA Journal, the top causes of healthcare data breaches are phishing attacks, ransomware attacks, and human error such as sending an email to the wrong recipient. A breach is defined as the unauthorized acquisition, access, use, or disclosure of protected health information (PHI) that compromises its security or privacy. Complying with HIPAA is almost a guarantee of preventing these data breaches. In addition to meeting data governance and security standards, ensuring the confidentiality, integrity, and availability of patients’ PHI is a must to maintain trust and security in the healthcare industry.
Three primary parts of HIPAA
To pull this off, the first thing to do is to understand the HIPAA rules and your role in there, whether you are a covered entity or business associate. There are three rules. By adhering to the Privacy, Security, and Breach Notification Rules, you put another brick in the wall of protection from data breaches. Let’s get closer to them:
- Privacy rule: It sets national standards for the protection of individuals’ medical records and other PHI, as well as limits on the use and disclosure of PHI by covered entities, ensuring that patients have control over their health information while permitting the necessary flow of data for healthcare delivery and payment processes. This rule establishes the rights of patients regarding their health information and regulates how covered entities (healthcare providers, health plans, and healthcare clearinghouses) use and disclose PHI. This Rule also requires covered entities to implement safeguards to protect the privacy of PHI and provides individuals with rights to access, amend, and obtain an accounting of disclosures of their health information.
- Security rule: It complements the Privacy Rule by establishing national standards for the security of electronic protected health information (ePHI). It requires covered entities and their business associates to implement administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of ePHI. The Security Rule mandates measures such as access controls, encryption, audit controls, and security incident procedures to protect ePHI from unauthorized access, disclosure, alteration, or destruction.
- Breach notification rule: It requires covered entities and their business associates to notify affected individuals, the Secretary of the U.S. Department of Health and Human Services (HHS), and, in some cases, the media, following a breach of unsecured PHI. The rule specifies the timeframes and requirements for reporting breaches, aiming to prompt timely action and mitigate the impact of data breaches on individuals’ privacy and security. Covered entities are required to conduct a risk assessment to determine the probability of PHI compromise and provide timely notification to affected individuals and HHS if a breach occurs.
There are also Omnibus and Enforcement Rules, which refer to the protection duration for up to 50 years following the death of a data subject and the procedures and penalties for enforcing HIPAA, accordingly.
HIPAA compliance officer
It could be a HIPAA compliance officer who would be responsible for overseeing and ensuring adherence to all HIPAA regulations within your organization. This person is crucial for maintaining compliance and minimizing the risk of data breaches and penalties. Moreover, this officer can cover, inter alia, the following important steps on your way to HIPAA compliance:
- Providing employee training and awareness: Ensuring that all employees are trained on HIPAA regulations and aware of their responsibilities is essential. The compliance officer will organize regular training sessions and awareness programs to educate employees on data privacy and security best practices for handling PHI.
- Maintaining documentation and records: Keeping thorough documentation of HIPAA compliance activities, including policies, training records, audit reports, and incident response documentation, is essential.
- Staying updated on regulatory changes: HIPAA regulations are subject to periodic updates and changes. The compliance officer will stay informed about any updates to HIPAA rules and ensure that organizational policies and procedures are adjusted accordingly to maintain compliance.
HIPAA compliance audit
Conducting a HIPAA compliance audit is an integral part of the compliance process. For your convenience, we made a HIPAA compliance audit checklist with a breakdown of HIPAA rules.
Privacy Rule audit checklist:
- Notice of Privacy Practices (NPP):
- Review and update NPP to ensure it includes all required elements.
- Verify that NPP is distributed to patients as per HIPAA requirements.
- Patient rights:
- Confirm that policies and procedures are in place to facilitate patient rights, including access to PHI, request amendments, and accounting of disclosures.
- Use and disclosure of PHI:
- Assess policies and procedures governing the use and disclosure of PHI, ensuring compliance with HIPAA’s minimum necessary standard.
- Verify that proper authorization is obtained for disclosures not covered under HIPAA’s permitted uses.
- Business Associate Agreements (BAAs):
- Review existing BAAs and ensure they meet HIPAA requirements.
- Confirm that BAAs are in place with all business associates handling PHI.
Security Rule audit checklist:
- Risk analysis and assessment:
- Conduct a comprehensive risk analysis to identify threats and vulnerabilities to PHI (ePHI).
- Document findings and implement mitigation measures based on identified risks.
- Administrative measures:
- Review administrative policies and procedures related to security management, including risk assessment, workforce training, and access control.
- Review procedures for responding to security incidents and breaches.
- Test incident response plans through simulated exercises to ensure effectiveness.
- Monitor access logs, security incidents, and compliance metrics to detect and address potential issues proactively.
- Physical measures:
- Verify controls such as access, device and media controls, workstation security, and facility access monitoring.
- Assess physical security means in place to protect facilities where ePHI is stored or accessed.
- Check controls such as access badges, surveillance systems, and secure locks to prevent unauthorized entry or theft of PHI.
- Technical measures:
- Evaluate technical controls implemented to protect ePHI, including access controls, encryption, and authentication mechanisms to restrict access to PHI based on user roles and privileges.
- Check firewalls, antivirus software, and intrusion detection systems to detect and mitigate cybersecurity threats.
- Ensure systems are regularly updated and patched to address security vulnerabilities.
Breach Notification Rule audit checklist:
- Breach identification:
- Review procedures for identifying potential breaches of unsecured PHI.
- Ensure staff are trained to recognize and report suspected breaches promptly.
- Breach notification process:
- Verify that a breach notification process is in place, outlining requirements for notifying affected individuals, HHS, and, if necessary, the media.
- Test the breach notification process to assess the timeliness and accuracy of notifications.
- Documentation and reporting:
- Document all breaches and responses in accordance with HIPAA requirements.
- Maintain records of breach notifications sent to individuals and regulatory authorities.
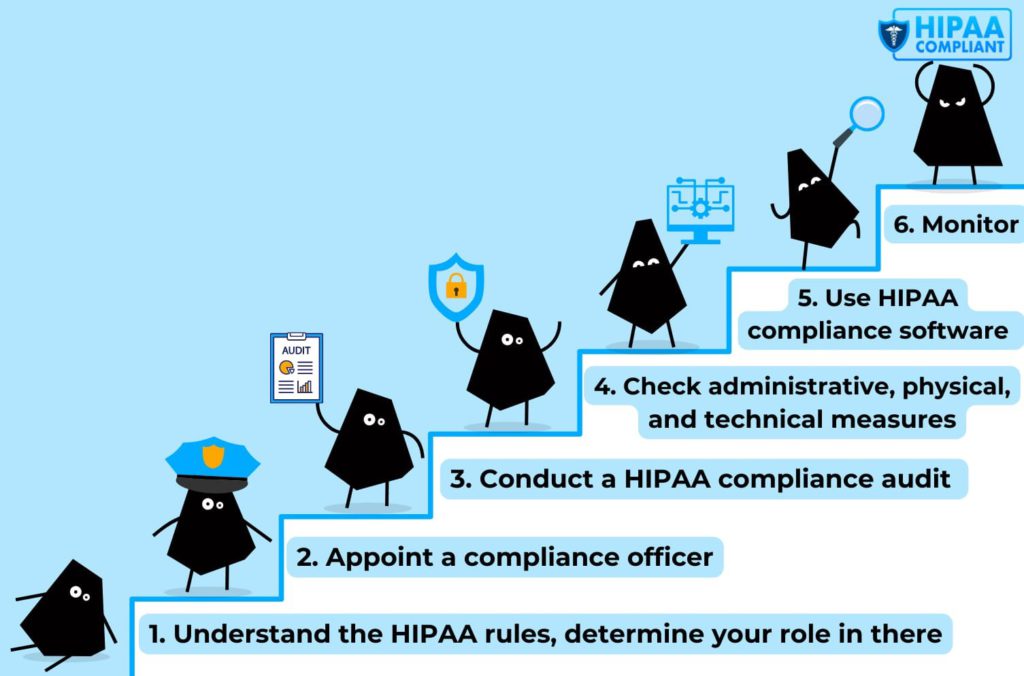
HIPAA compliance software
To help you more in the HIPAA compliance journey, we encourage using HIPAA compliance software, designed to automate and centralize compliance management processes. These software solutions offer features such as risk assessment, policy management, employee training tracking, and incident response planning, providing a comprehensive framework for maintaining compliance with HIPAA regulations. By leveraging HIPAA compliance software, healthcare entities can enhance efficiency, mitigate risks, and demonstrate a proactive commitment to safeguarding patient data.
HIPAA compliance database
For example, the management and protection of PHI necessitate robust database solutions that comply with HIPAA regulations. HIPAA compliance databases offer features such as data encryption, access controls, audit trails, and regular backups to safeguard sensitive patient information. These databases ensure that PHI is stored securely, accessed only by authorized personnel, and maintained in accordance with HIPAA guidelines. By deploying HIPAA compliance databases, healthcare organizations can enhance data security, contribute to interoperability, streamline compliance efforts, and mitigate the risk of data breaches or unauthorized disclosures.
AWS HIPAA compliance
Cloud computing services, such as Amazon Web Services (AWS), have also emerged as critical enablers of HIPAA compliance. We, as an AWS Select Consulting Partner, recommend AWS, which offers a HIPAA compliance program, providing assurances that its cloud infrastructure meets the security and privacy requirements outlined in HIPAA regulations. Covered entities can leverage AWS HIPAA compliance to securely store, process, and transmit PHI, leveraging scalable and cost-effective cloud solutions without compromising on data security. However, it’s essential for healthcare organizations to implement proper configurations and safeguards to ensure compliance when using AWS or any other cloud service provider.
HIPAA-compliant telehealth platforms
After the COVID-19 pandemic, the demand for telehealth services has surged, prompting the adoption of HIPAA-compliant telehealth platforms. These platforms facilitate remote patient consultations while adhering to stringent security and privacy requirements mandated by HIPAA. Features such as end-to-end encryption, access controls, and secure data transmission ensure the confidentiality and integrity of patient information during virtual visits. Moreover, HIPAA-compliant telehealth platforms enable healthcare providers to expand their reach, improve patient access to care, and enhance personalized care.
Conclusion: Become HIPAA compliant with the HIPAA compliance checklist and HIPAA compliance consulting services
That’s it. By adhering to our guidelines, you can not only meet regulatory standards but also foster a culture of trust, transparency, and patient-centered care. However, this checklist is not exhaustive. Do not forget about continuous monitoring of the whole thing! If you want to fully protect yourself in the context of HIPAA compliance, book a meeting with us to learn how our HIPAA compliance consulting services can benefit your business. See you soon!